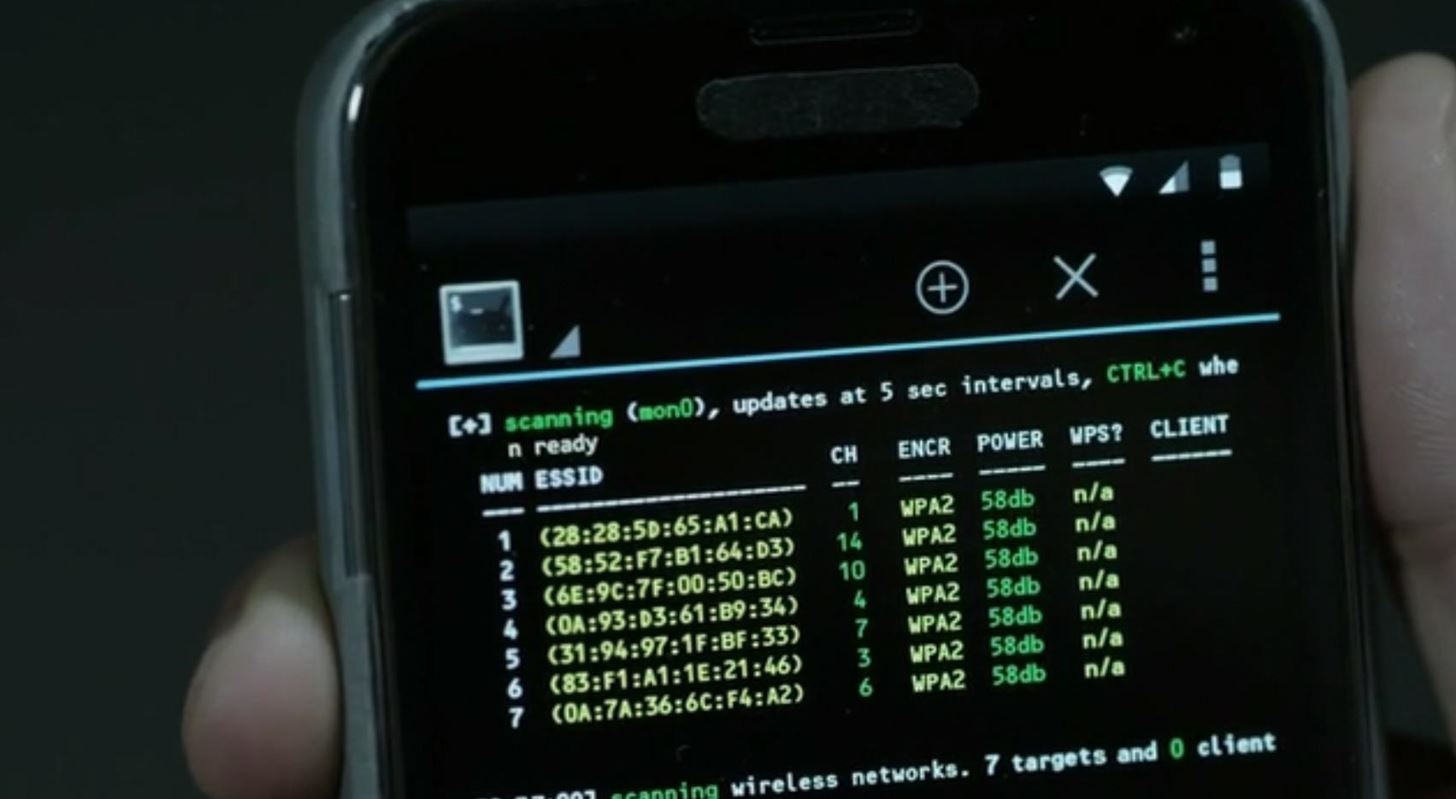
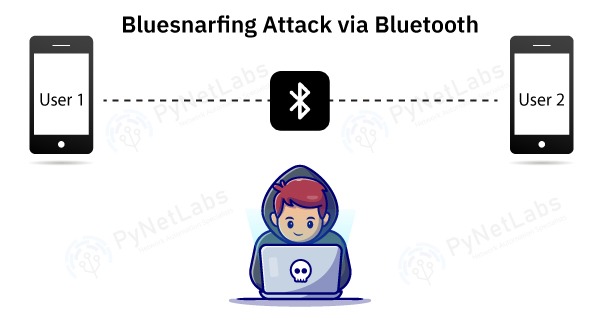
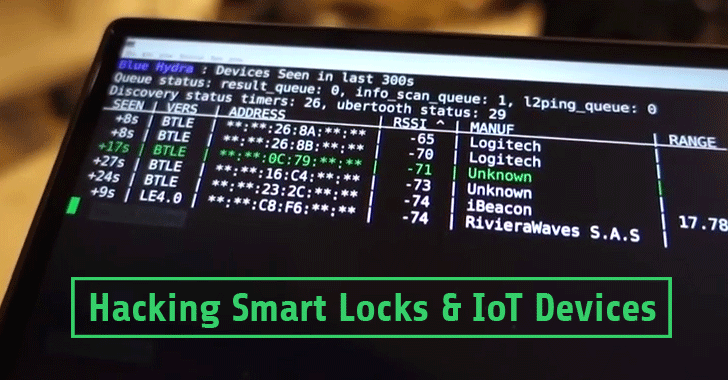
Avoiding WiFi and Bluetooth Hackers in Your Home | Business and Home Security Solutions | Northeast OhioAvoiding WiFi and Bluetooth Hackers in Your Home

Using TWS or Bluetooth devices? Here's how you can safeguard yourself from Bluetooth hacking - India Today

Chanakya_Mandal on Instagram: "Preventive Measures Against Bluebugging Hacking: Turning off Bluetooth and disconnecting paired Bluetooth devices when not in use. Making Bluetooth devices undiscoverable from Bluetooth settings. Updating the device's ...

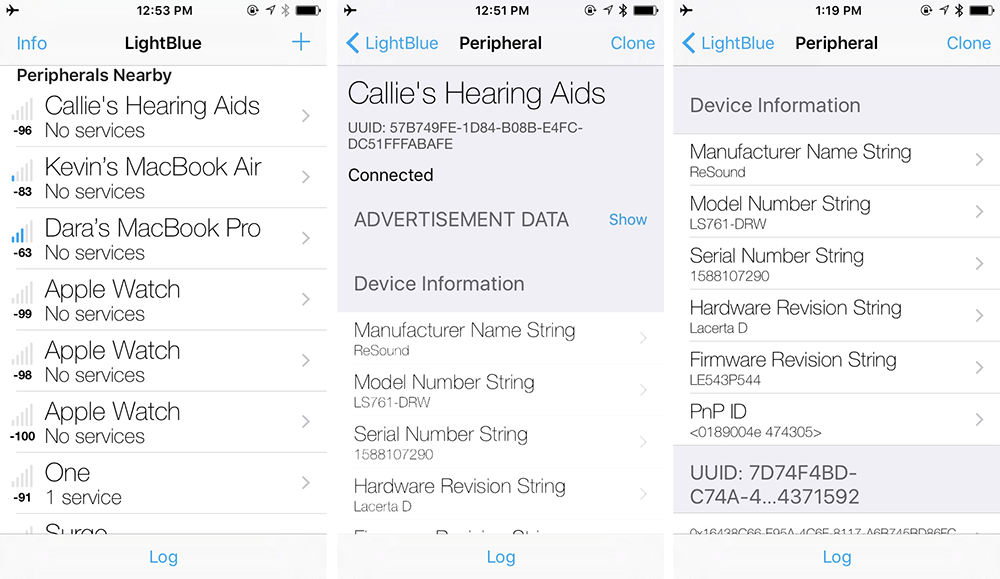
How to hack Android, macOS, iOS, and Linux through a Bluetooth vulnerability | Kaspersky official blog